Edward Snowden: 10 years on
The more things change, the more they stay the same. Here's what you can DO about it.

IMPORTANT UPDATE (December 2023):
I have come across some very disturbing information concerning some of the services recommended by
as well as the person himself.In the meantime however, I am formally withdrawing my recommendation of Signal Messenger due to them receiving almost 3 million dollars in funding from the Open Technology Fund which is part of the global network run by the US Agency for Global Media, which is part of the US federal government.
Signal is also facing an uncertain future due to funding cuts from their ‘sponsors’.
provides the rundown in this article:Also this:
The section discussing Signal has now been deleted. DO NOT USE SIGNAL!
On June 6 2013, investigative journalist
broke a story about how the US National Security Agency (NSA) was running a top-secret program which amongst other things, was collecting the phone records of millions of American citizens without their consent or approval and without them being convicted of any crime or even being suspected of one.The article ended with an ominous quote from Senator Frank Church who was the chair of a committee set up by the US Congress in 1975 to investigate the activities and scope of surveillance operations by the CIA, FBI and the NSA, which since its formal creation in 1952 had a very clear stipulation in its charter to never conduct any surveillance domestically:
The NSA's capability at any time could be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn't matter.
Senator Church’s conclusion in 1975 proved to be prophetic beyond the wildest dreams of anyone, including his own!
Two days later on June 8, Mr. Greenwald broke another story about a program called PRISM which gave the NSA direct access to the servers of Google, Apple, Microsoft and Facebook, as well as a few other unnamed tech companies.
The story included several slides from an internal NSA Powerpoint presentation which explained how PRISM operated and also revealed it has been in operation since at least 2007 (so for at least 6 years by the time the news about it became public).
All the big tech companies mentioned in the story denied any knowledge or involvement in the program despite the fact that the NSA’s own slides made it clear that while PRISM was a highly classified program, it was conducted with the full knowledge and cooperation of the tech companies involved.
Despite the prohibition in NSA’s charter to conduct any surveillance operations within US borders, the existence of PRISM was enabled by changes to US surveillance law introduced under President Bush and renewed under President Obama in December 2012.
Greenwald didn’t provide any information about how he obtained this information and the internal NSA slide deck but said that there was absolutely no doubt it is 100% authentic.
He also said that he will not give any further information about his sources (as any journalist is expected to do) other than saying it is “rock solid”.
Two days later, Greenwald’s source publicly revealed his identity as
, an employee of defence contractor Booz Allen Hamilton who worked at both the CIA and the NSA as a contract analyst.A day after Snowden publicly revealed himself as the source of the leaks, Glenn Greenwald and his colleague Ewen MacAskill blew the lid on another NSA program disclosed by Snowden and which made PRISM look like a kid’s toy in comparison.
It was called Boundless Informant.
Boundless Informant was a data mining tool which was used to catalogue surveillance data obtained through the myriad of the NSA’s surveillance programs by using the metadata contained in them.
In simple terms, it was basically an internal search engine for surveillance data obtained by the NSA.
The most explosive revelation about Boundless Informant was the scope and breadth of NSA’s surveillance programs and the almost unimaginable volume of data programs such as PRISM collected.
Just to give you an idea, the NSA’s internal documents about Boundless Informant which were leaked by Snowden showed that the agency collected 3 billion pieces of data on US citizens during March 2013 alone!
Let that sink in and then try to imagine what capabilities the NSA has 10 years later given the huge advances in computing power, AI and machine learning that have occured since.
Just over a month later Glenn blew the lid on another NSA surveillance program which eclipsed both PRISM and Boundless Informant.
It was called XKeyscore.
The NSA’s internal PowerPoint presentation on XKeyscore which was also included in Snowden’s data dump showed that, as of 2008, this tool was able to, according to their own words:
"Collect nearly everything a typical user does on the internet"
This included the content of emails, social media posts, web browsing activity and any and all metadata about the user.
This data was able to be collected in real-time on every single Internet user on the planet and NSA staff didn’t need to get any permission from anyone before sifting through this treasure trove of data which often contained highly sensitive and private information about individuals!
After Snowden came out publicly as the NSA whistleblower, things have started to move very quickly from that point onward and the rest as they say, is history…
A decade later, Ed Snowden is still stuck in Russia, a country he never intended to settle in or even enter.
The Significance of the Snowden revelations
While there have been many leaks and disclosures of nefarious activities by various US government agencies over the years prior to that point, none have even come close to the scope and significance of what has been revealed by Snowden.
A recent article by the Electronic Frontier Foundation, one of the leading global organisations dedicated to protecting people’s civil liberties online, put it best:
Snowden’s revelations acted like a flood light, allowing everyone to better see and understand what happens inside the black box of government surveillance of millions of innocent people in the US, and around the world.
The tremendous amount of evidence slowed, if not stopped, the disingenuous denials that the government had made both publicly and privately in response to our allegations.
The actual documentary evidence also helped us to better pinpoint our demands, our questions, and our legal tools.
Snowden himself also explained in a very eloquent way how such programs pose grave threat to the freedom of people globally, as well as the very integrity of the Internet, in a viral 2014 TED Talk he gave, appearing through a screen on a robot with a camera whose movement he controlled remotely.
He was unable to attend in-person due to the US government cancelling his Passport and issuing a global arrest warrant against him, stranding him in Russia to this day.
Government surveillance of the Internet has only become more pervasive since
Many people (myself included) thought that the Snowden revelations in 2013 will mark a watershed moment and the US government, as well as other governments of the so called ‘free world’, will now be compelled to reign in their intelligence agencies by putting clear rules about what they are allowed to do (and even more importantly, what they cannot do) and then put mechanisms to ensure these rules are strictly enforced.
Unfortunately, the reality of the last 10 years is that, while some progress has been made, such surveillance programs not only didn’t disappear but have actually become much worse, especially on social media.
The Twitter Files saga this year was one of the most public culminations of that surveillance and interference by governments and their intelligence apparatus.
I would also argue the intelligence apparatus in western ‘democracies’ has become an uncontrollable beast over the last decade and is now the one that is in control over the elected government, instead of the other way around.
This is what is referred to by many as the deep state. A permanent and unelected power structure sitting in the shadows and answerable to no one, least of all the people!
At this stage of the game and knowing what we know now, I’d argue that the only way to fix the predicament we are in with regards to this completely unaccountable “deep state” apparatus is to take the approach which John F. Kennedy vowed to take before he was assassinated:
“I want to shatter the CIA into 1000 pieces and scatter it to the winds!”
The same should apply to the NSA, FBI, NRO,DHS and all the other three letter agencies of the US government, as well as their counterparts in other countries.
How can you fight back against surveillance by governments and their intelligence apparatus?
I’d argue that as things stand now, the most dangerous adversary (or “threat actor” as it is referred to in the Cybersecurity industry) for the average citizen is their own government and the last three years have proven that definitively!
The 40th US President Ronald Reagan has put it best when he said:
The nine most terrifying words in the English language are "I'm from the government, and I'm here to help."
So what can one do to protect their privacy online from snooping by governments?
Well, the answer is comprised of two main aspects:
Encryption - making your data and activities hard to read even if intercepted; and
Decentralisation - making your data and activities hard to intercept in the first place due to the fact it is spread across multiple servers and physical locations.
I will outline below some practical solutions, which I have been using myself for at least two years now, and which incorporate one or more of the above. All of these solutions can be accessed relatively easily by anyone and even if you are not tech savvy.
However, before I do that, allow me to touch on one other very important aspect which quite a few people I come across still don’t quite get.
Privacy matters!
Ten years after the Snowden revelations and even after the last three years of unprecedented government overreach and surveillance, I still often hear people saying something along the lines of:
“I am not really concerned about privacy because I am a law abiding citizen and have nothing to hide”.
There are two main problems with the above statement:
Privacy is a fundamental human right formally defined as such in the Universal Declaration of Human Rights as well as article 17 of the International Covenant on Civil and Political Rights (ICCPR). This should make it very clear to any reasonable person that protecting the privacy of the individual is important, even if you yourself don’t care about it much personally. This leads me to the second problem which is…
Allowing a human right like privacy to be breached opens the door to other basic human rights being trampled on as well. Edward Snowden put it best himself when he said the following:
So now that you are hopefully convinced that privacy is important, let’s look at a few solutions that are available to you today.
All the solutions below offer very strong encryption and some are also decentralised which is the ultimate protection not just from governments but also from malicious hackers and cyber criminals.
Encrypted email
Even with the advent of instant messaging and social media, Email is still the most popular use case of the Internet.
What you may not be aware of is the fact that email is an inherently insecure means of communication and therefore you should be extremely careful about sending private information through email.
Most of the big email providers have introduced in recent years encryption for email while its in transit which does make email slightly more secure but that doesn’t protect your emails from being snooped on by those very same email providers (although they ‘promise’ they don’t do it. Pinky swear) as well as intelligence agencies who, as Snowden has shown in a very stark way, can and do spy on people’s emails even without their consent or a court order.
The best way to keep your email private is to:
Use an email service with strong encryption;
Use an email service which has technical barriers in place to prevent it from reading its users emails; and
Use an email service whose business model/Unique Selling Proposition revolves around keeping users emails private.
That third point above means that any email service which is completely or predominantly free should not be used.
This rules out straight away all the big players like Google (Gmail), Microsoft (Outlook/Hotmail) and Yahoo.
While these services offer a very decent storage allowance and good usability, they are also the ones behind the concept of Surveillance Capitalism which can best be summed up as:
If you’re not paying for a product, you ARE the product!
Just in case you need any more reasons not to use them, they are all “technology partners” of the World Economic Forum and their founders are confirmed co-conspirators in the COVID-19 Plandemic and the rollout of the weapons of mass genocide and genetic manipulation commonly known as the C19 injectables.
Here’s what you should use instead:
Tutanota
Important update:
Tutanota has posted the following on their official Twitter account:
This may rule them out for you if you are opposed to the trans agenda and its attempts to sexualise kids.
I am personally evaluating my options as a result of their Twitter post and will likely switch to Mailfence. The video below outlines their main features when it comes to privacy and security.
Tutanota (which means“secure message” in latin) has been around since 2011 and are based in Germany.
They started initially as provides of encrypted email but have since expanded to also offering an encrypted calendar as well as encrypted email service for businesses.
As of this month (June 2023), they have gone past the 10 million users mark.
While this is nothing compared to the major providers, it means they have a good product and a sustainable business model which essentially means they are here to stay!
I’ve been using this service myself for almost four years now and have nothing but praise for them.
They have also publicly committed to ensuring their encryption is resistant to attacks facilitated by quantum computers. Without getting too geeky, this means they are actively working on making sure the emails that go through their systems remain encrypted even when an attempt is made to decrypt them by much more powerful computers than what we have access to today.
This is especially pertinent given governments and their intelligence services almost certainly already have access to such computers, whether they admit it or not!
Tutanota provides 1GB of storage for your emails for free with all the security features paid accounts have. This means you can try out their service for free for as long as you want and only upgrade when you’re ready to make them your primary email provider (which I strongly recommend you at least consider).
Another encrypted email service that is very popular and widely used by freedom activists is Protonmail.
Protonmail is based out of Switzerland which is a neutral jurisdiction that is not part of NATO, the EU or any major intelligence gathering alliances (unlike Germany where Tutanota is based) and offers very similar prices to Tutanota, including a free account with 1GB of storage.
This all sounds great and I understand why many in the so called “freedom community” have chosen to use the service, as well as recommend it to others.
There is just one ‘slight’ problem:
Proton, which is the company offering the Protonmail service is a partner of the World Economic Forum, which is also headquartered in Switzerland!
For me personally, this rules them out completely as a potential option to even consider.
If that’s not enough of a concern for you, here are a few more:
Encrypted Cloud Storage
People like to backup files to the ‘cloud’ which makes accessing them on the go much easier and also ensures they are not lost in case your local machine or external hard drive/USB stick gets damaged or stolen.
The biggest players in the cloud storage space (at least when it comes to individuals needing a service for personal use) are Google Drive, Microsoft OneDrive and DropBox.
As I mentioned previously, both Google and Microsoft are “strategic technology partners” of the World Economic Forum, their founders are confirmed co-conspirators in the Plandemic and their leadership are regular attendees at the Bilderberg meetings.
With regards to DropBox, their CEO is a WEF Member and the company also appointed former US secretary of state Condoleezza Rice, a well known operative of the ‘deep state’ to their board.
Most importantly: the consumer (i.e ‘free’) version of their cloud storage products is not encrypted at all by their own admission.
Here’s what you should use instead:
Tresorit
Tresorit is a secure cloud storage service based out of Switzerland which has been around since 2011 and in 2021 has been bought by the country’s postal company.
They have an extensive range of security features, key amongst them is what’s called “Zero-knowledge architecture”.
Again, without getting too technical, all you need to understand is that with such architecture, it is technically impossible for anyone other than you, including the company itself, to decrypt any of the files you store on their service, even if they wanted to or were compelled to do so by a government order.
Tresorit no longer offer any free plans but you can try out any of their paid plans (which are very competitively priced when compared against the major providers) for 14 days to see if this works for you.
Internxt Drive
If you don’t like the fact Tresorit doesn’t have a free plan or find their prices too expensive (keep in mind you’ll definitely be paying more with any of the majors), you may want to check out Internxt Drive which I have been using for around 18 months now.
Internxt is a cloud storage service based out of Spain and is definitely still at the start-up stage (unlike Tresorit which is already well established and profitable).
This means that their long term survival is far from guaranteed and I can also say from personal experience that their software does have some bugs and quirks from time to time (although it has improved in leaps and bounds when compared to even 12 months ago).
Just like Tresorit, they also offer extensive security and privacy features including “Zero-knowledge architecture” and “End-to-end encryption” which means that every file you upload to their service is always encrypted as it moves to and from their servers (known as “in transit” encryption) as well as when it is stored on their systems (known as “at rest” encryption).
Another thing they do, which Tresorit does not, is break each file into multiple components as it’s uploaded to their system, which are then kept separate from one another.
The only way to put the file back together so to speak is through the software (desktop client of mobile app) used by the specific user who uploaded that file. While this may sound very complicated, I can assure you that the way this happens in the software is very easy and completely invisible to the user.
Internxt offers a ‘free forever’ plan with 10GB of storage with paid plans that are extremely cheap, especially when looking at annual prices.
They also have lifetime plans whereby you pay once and that’s it with prices starting from 299 Euros for 2TB of storage.
This is extremely cheap but as I said before, no guarantee that the company will be around for an extended period of time and remember that any “lifetime” plan you buy is for their lifetime, not yours… ;)
Encrypted Instant Messaging
Instant Messaging (IM) is now the second most popular use case of the Internet (second only to email) and as its popularity grew, so did the number of IM services available to you.
The biggest players in this space are iMessage by Apple (mainly due to the fact that it comes pre-installed on every iPhone or iPad), Facebook Messenger and WhatsApp, which has also been owned by Facebook/Meta since 2014.
During the pandemic and as censorship/gaslighting by governments and ‘big tech’ ramped up, another IM service exploded in popularity and has become the tool of choice for so called “freedom groups” everywhere: Telegram.
People initially chose Telegram because it was deemed as very easy to use (which is kinda true) as well as secure and encrypted (which is absolutely not true!).
The problem with Telegram is not only that it is actually not encrypted by default, with both its channels and groups being especially vulnerable, but also the fact that it, together with another IM service called Discord, has become the platform of choice for hackers to infect computers and phones as well as to steal user data.
Furthermore, the creator of Telegram, as well as the CEO and majority owner of the company behind the service is a Russian Billionaire by the name of Pavel Durov, often referred to as the “Zuckerberg of Russia” due to the fact he was also the creator of VKontakte (VK), the “Facebook of Russia”.
Durov has a very interesting personal and professional history which I may touch on in another post but one thing that is especially of note is the fact he is a proud member of the World Economic Forum!
Still comfortable with using Telegram?
If not, here is what you should use instead:
Session
Session is operated by the Session Technology Foundation based out of Switzerland.
They are affiliated with another great project which I will touch on a bit later when I talk about VPNs but for now, let’s focus on Session itself.
Session provides one-on-one messaging, group chats, and voice calls. No video calls available through Session just yet but it’s in the works.
As the slick promo video above explains, Session key strengths are:
No phone numbers (or emails or anything really that can identify you to an external party); and
A completely decentralised architecture. There is no central server to spy on, attack or shutdown.
The above two points (as well as a few more ‘geeky’ details) mean that Session offers censorship resistance which is UNRIVALLED by any other Instant Messenger, at least amongst those who are not aimed exclusively at hard core geeks and cyberpunks.
The creators of Session took the existing Signal protocol and made it better or, as they say in their own whitepaper:
The creation of Signal provided a big step forward for private, secure communication. But even Signal suffers from some key privacy weaknesses.
While it laid excellent groundwork, the private messaging space still lacked an application which truly made no privacy compromises.
Session is that application. It’s purpose-built for those who are privacy conscious or need to communicate sensitive information over the internet.
When users sign-up to Session, their device generates a cryptographically secure Session ID. This is used as their contact information on the app.
No personal information is required to create a Session ID, so you never need to link your real identity to your identity on Session. Session IDs are the public half of a public/private key pair, making them secure, recyclable, and anonymous.
The private half, which is known as your Recovery Phrase, can be used to restore your Session ID on a new device.
Session IDs give users a simple way to contact each other as well as being a part of Session’s end-to-end encryption protocol.
Because Session IDs are public keys, they can be used to encrypt a message which only the owner of that ID can decrypt.
By using the keys themselves as contact information, man-in-the-middle attacks that exploit contact registries are impossible, and users have an assurance their messages will remain private and secure.
By restricting the creation or collection of metadata or identifying information about its users, Session also gains censorship-resistant qualities.
Because individual users in one-on-one and encrypted group chats cannot be identified, they cannot be personally targeted by censorship from third-parties.
Hopefully the above is not too technical and helps you understand why Session is superior to even a service like Signal when it comes to both privacy and security.
But Session have taken it one step further by using a completely decentralised architecture.
Or in their own words:
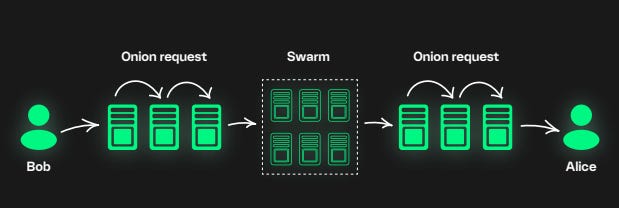
Session utilises the decentralised Oxen Service Node Network to store and route messages.
This means that unlike P2P messaging applications, you can message Session users when they are offline.
The Service nodes, which are stationed all over the world, are organised into collections of small co-operative groups called swarms.
Swarms offer additional redundancy and message delivery guarantees even if some service nodes become unreachable.
By using this network, Session doesn’t have a central point of failure, and Session’s creators have no capacity to collect or store personal information about people using the app.
Every encrypted message is routed through three nodes in the Oxen Service Node Network, making it virtually impossible for the nodes to compile meaningful information about the users of the network.
When a message is sent, one node will know the sender has sent a message—but not know its destination—and a different node will know the receiver has received a message—but not know its origin.
I don’t want to get any further into the technical details as they are very complex and will likely only confuse you (but feel free to do so yourself if you’re interested) and will only say that if Signal is the “gold standard”, according to Snowden, of secure and private Instant Messaging, Session is the ‘Diamond standard’ in my opinion.
If you’re still curious about how Session’s decentralised network actually works and want an explanation in non-technical terms, they have a video just for you.
Finally, in 2021, OPTF which were the previous stewards of Session, paid to have Session independently audited by Quarkslab, a cybersecurity company specialising in Application Security (AppSec).
The results of this audit, as summarised by Quarkslab themselves are as follows:
Oxen's Session really improves Signal privacy and resilience by adding an overlay network to the existent end-to-end encryption instant messaging solution.
The onion-routing mechanisms make use of Oxen’s Snodes to store and exchange messages, however, there are some other centralized standard web services that are still used through the overlay network (for the push service and to deliver attachment files).
The overall security level of this application is good and makes it usable for privacy-concerned people.
If you are technically minded and want to have a look at the full audit report yourself, it can be found here.
I literally cannot fault anything about this service when it comes to both privacy and security and because of how it is built, the identity of the people and organisation behind it almost doesn’t matter.
However, I did do a bit of digging before I started using this service around 18 months ago and really couldn’t find anything to worry about the foundation, its people or any of their past associations.
Following a direct question regarding funding sources (which is probably the single most important question about any project!), Chris McCabe, who is the co-founder and CEO of OPTF, had this to say regarding how they fund their operations:
We raised 9 Million USD in 2018 from investors in a private sale.
In 2021, we spun off Chainflip, and the OPTF is a major stakeholder in that, resulting in substantial funding for the OPTF.
The foundation receives a token reward and stakes service nodes.
The OPTF is a non for profit foundation set up in Australia, so all profits and income to back into the project.
They also regularly publish transparency reports showing how many requests they received to provide data about their users and how many of those they complied with.
Here is the most recent one:
If you are ready to jump in (which I strongly encourage you to at least consider), the video below covers everything a potential newbie needs to know and as you’ll see, despite the underlying tech being quite complex, the user experience is very good, even for non-geeks.
Private Web Browsing
A Browser, whether on your computer or your mobile device, is the primary ‘vehicle’ we all navigate the Internet with.
It is almost certainly one of the applications you spend the most time in while online and therefore, has the potential to collect the most information about you through what you enter on various websites (name, address, password and credit card details) as well as through the details of the websites you visit through your browsing history.
Furthermore, the browser is what allows websites to collect data about you through cookies and various trackers and so called web beacons.
Just like with most other software and online services, the browser market is entirely and completely dominated by ‘big tech’ with Chrome by Google and Safari by Apple used by more than 80% of people globally to browse the web.
Firefox, which still manages to stay in the list of top browsers (just), is often touted as privacy-minded browser but this is not the case and hasn’t been for a long time!
To add insult to injury, Mozilla which is the organisation behind this browser is a partner of the World Economic Forum.
Did you know that already? If so, Kudos to you!
As you probably gathered, all the browsers you see in the image above are out of the question.
Here is the one to use instead.
Brave
Brave, just like Google Chrome, is based on the Chromium open-source browser project which means that most browser extensions that work in the Chrome browser, will also work in Brave.
This is where the similarities between the two end though as Brave doesn’t just differ from Chrome in technical aspects but more importantly, in its very philosophy.
While Google (a strategic WEF technology partner and willing accomplice to any government attempt to spy on its people), as a founding member and major participant of the ‘surveillance economy’ mentioned previously, uses the Chrome browser first and foremost as a data collection tool, Brave’s entire business model revolves around protecting the privacy of its users and only serving them ads if they willingly and explicitly asked for it…and even then without actually trying to collect any personally identifying data on them.
To get a better understanding of Brave’s business model and underlying economics, watch the video below in which the Brave founder and CEO Brendan Eich explains it.
As you will find out in the first few seconds of the video below, Mr. Eich is literally one of the founding fathers of the web and his past track record shows that if he says he is out to do something when it comes to our online world, he means it!
Brave and the Basic Attention Token (BAT), which is the economic model on which Brave runs, may just be his most ambitious project yet and he is right when he says that Brave and BAT are “the future of advertising on the Internet”.
One of the ‘killer features’ that Brave has when it comes to Privacy is the ability to use the functionality of The Onion Router (TOR) without having to download the browser itself which is something that may be blocked by your government or at the very least, put you on their radar.
In early 2023, Brave has made this feature even more powerful by allowing people to circumvent any blocks or filtering their Internet provider or government may have introduced to block access to the Tor service.
Brave is really a browser like no other and while there are other privacy-focused browsers out there, none have the usability and set of features that Brave offers.
Furthermore, none of them have a true ‘giant’ of our times in the form of Brendan Eich at the helm.
Brave is available for all computers and mobile devices in use today.
It was also judged as the most private browser by the team at Session which is discussed above:
Private Search Engine
Just like the browser, A search engine is an essential tool for navigating the vastness of the web.
And also just like the browser, using the wrong search engine means an insane amount of information can be collected about you based on what you’re searching for and what you click on.
Worse yet, the search results you get can become the deciding factor on how you perceive the world around you and what actions you take (or refrain from taking) which can be very dangerous and even outright deadly!
Therefore, you must be very careful with your choice of search engine and anything you go with must meet the following two criteria, which are completely non-negotiable:
The search engine must not track you in any way; and
The search engine must not attempt to manipulate the search results you receive in order to push a certain narrative, agenda or commercial interest (other then when serving ads which are clearly marked).
The first name that comes up by default in most people’s mind when thinking about a private search engine is DuckDuckGo which has been around since 2008.
Now, while it is true that DuckDuckGo doesn’t track or record your search history, doesn’t build a user profile on you and doesn’t contain third party trackers on its search engine, its mobile browser, which they advertise as “privacy-focused” has some major privacy issues in it.
But that’s not the biggest issue in my opinion.
Instead, the main issue is the fact that DuckDuckGo has publicly walked away from providing unbiased and non-manipulated search results. This means by definition that they no longer meet the second criteria above and therefore should not be considered in my humble opinion as a viable option for a search engine.
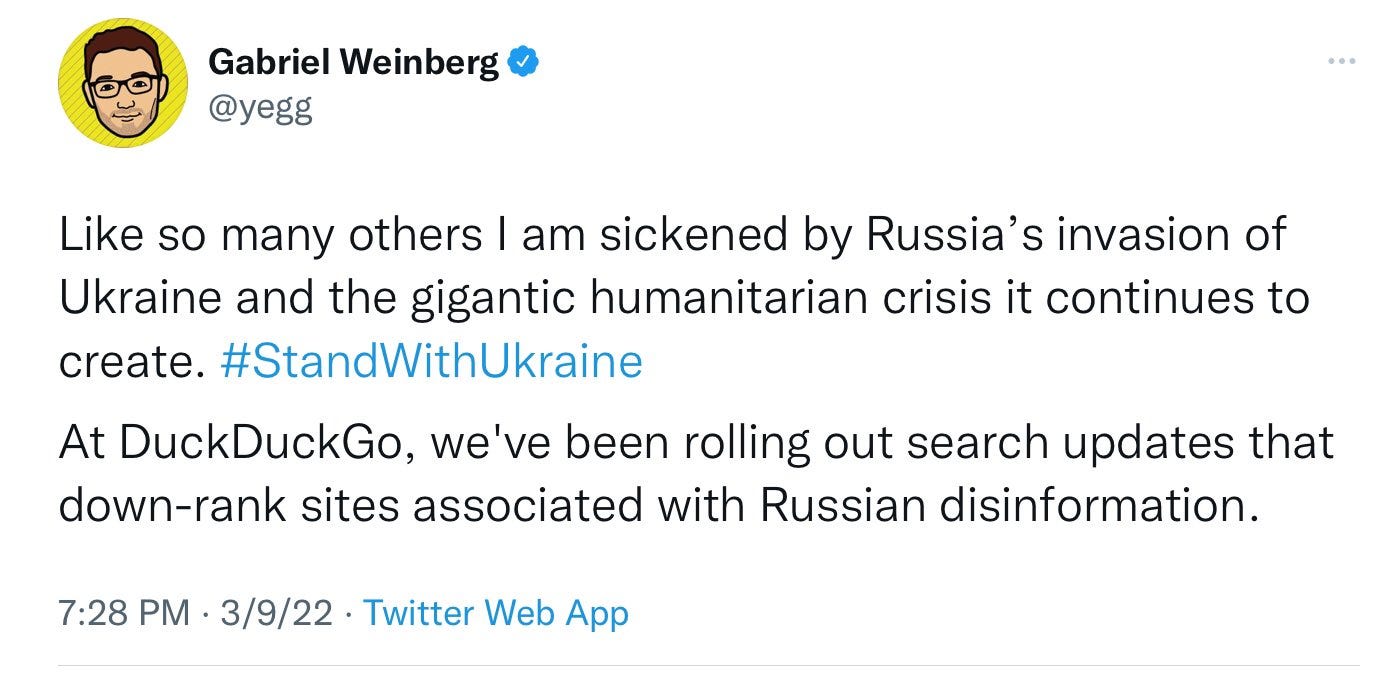
Here is a Tweet their Founder and CEO put out in March 2022 as the Russia/Ukraine conflict started:
This is a very problematic statement as who is the one deciding what is “disinformation”?
Is it the search engine (problematic), some so called “fact checkers” (very problematic) or the government (super duper problematic)?
Furthermore, as we have all seen over the last few years, so called “Disinformation” around COVID-19 which got aggressively censored, can and usually does eventually prove to be the truth. Even the self proclaimed “America’s Newspaper” openly admits it now!
Furthermore, if one has decided to censor so called “disinformation”, this needs to apply to all disinformation, even if it’s coming from the US government and its NATO allies.
This decision by Weinberg has resulted in a very strong backlash and rightfully so! Given the DuckDuckGo search engine doesn’t really have any killer features other than being private and unbiased (which this decision clearly shows to be no longer the case), I personally can’t see how the company will survive going forward, especially when also taking into account that their “privacy-focused” mobile browser also doesn’t seem to be private at all.
They will either get bought out or just close down but either way, a much better alternative for a search engine that is both private and unbiased is already here and thanks to DuckDuckGo essentially shooting themselves in the foot, it has gained a lot of prominence and popularity over the last year.
This alternative comes from the same people and company which gave us the Brave browser.
Brave Search
Brave’s search engine is built into their browser and enabled by default but even if you don’t use the Browser, it is accessible to anyone through the URL:
https://search.brave.com/
Brave Search was launched in June 2021 and right off the bat has experienced explosive growth reaching 2.5 billion searches in the first year alone, mostly due to their explicit promise to be:
A privacy-protecting, unbiased alternative to Google and Bing, and a truly independent alternative to providers—such as DuckDuckGo or Startpage—that rely on Big Tech to run.
In March this year (2023), Brave Search introduced a new AI tool called the Summarizer with the goal of providing:
Concise and to-the-point answers at the top of Brave Search results pages, in response to the user’s input, solely based on Web search results.
Unlike a purely generative AI model, which is prone to spout unsubstantiated assertions, we trained our large language models (LLMs) to process multiple sources of information present on the Web.
This produces a more concise, accurate answer, expressed in coherent language.
If you are not entirely convinced yet to make Brave Search your first choice when it comes to searching the web, hopefully the video below will seal the deal:
Virtual Private Network (VPN)
A VPN is another essential tool everyone should have in my opinion when being online.
In the most simple terms and without getting technical, a VPN essentially creates a secure tunnel through which data travels to and from your computer or mobile device.
This secure tunnel should at the very least:
Keep the data going through it private from the outside world, including snooping by governments and their intelligence apparatus; and
Keep the data going through it private from the VPN provider themselves.
VPNs have exploded in popularity over recent years due to both privacy and security concerns but also in order to bypass geo restrictions on various streaming platforms which prevent people from accessing content that the provider of the streaming service hasn’t licensed.
One potential disadvantage with VPNs that I want to mention from the get-go is the fact that using one will almost always result in somewhat reduced connection speed, especially if the VPN provider doesn’t have the fastest network or a server in close physical proximity to you.
The size of the VPN industry last year (2022) was 44.6 billion US Dollars and it estimated to almost double by 2027. It’s BIG business!
One of the biggest VPN providers out there is NordVPN. They are big because they really do have a good product and offer decent value for money.
The problem is that they are also a “technology partner” of the World Economic Forum (WEF).
Another provider which has been getting a lot of popularity in recent years is ProtonVPN, mainly due to their very generous free plan.
ProtonVPN is made by the same company which provides the ProtonMail secure email service which is also, as I mentioned previously, a WEF “technology partner”.
This rules out both of these providers for me personally.
Here is what I use instead:
VPN for the computer: Lokinet
Lokinet is made by the same people who make the Session messenger I mentioned previously and run on the same decentralised architecture of Oxen Service Nodes.
Just like Session, it is completely free to use as the economic model relies on incentivising the operators of the service nodes instead of the end users using a native cryptocurrency token.
Their VPN client software is available for Windows, Mac and Linux and I honestly can’t fault it.
It is extremely easy to use (literally one button to turn the VPN on or off) and light on resources although, like all other VPNs, you will notice a much slower connection speed which may make things like watching videos a bit annoying.
VPN for the mobile
Lokinet doesn’t have a mobile app just yet so if you want a VPN for your phone or tablet, you will need to look elsewhere.
I used to use TigerVPN, based out of Slovakia, for over 4 years but unfortunately they went out of business in the middle of last year.
I am yet to decide on my permanent replacement and have been using various technical workarounds while testing a few options.
I have narrowed down my research into two options which I am yet to decide between:
Brave VPN & Firewall - offered by the same people behind the Brave Browser and Brave search; and
Orchid - a decentralised VPN service paid for using cryptocurrency.
The Snowden Legacy
There is absolutely no doubt Ed Snowden is one of the most important whistleblowers in modern history and definitely on the same level as Assange, Manning and FBI Associate Director Mark Felt, better known under the alias “Deep Throat” given to him by Woodward and Bernstein, the two investigative reporters from the Washington Post who broke the Watergate story in 1972.
Unfortunately, many people still can’t see the importance of his revelations.
They are also unwilling to punish big technology companies for the many absolutely egregious privacy violations they have committed, and continue to commit every day.
CitizenFour
In 2014, Laura Poitras released a documentary about Snowden which documented in great detail the events leading to, during and following his revelations.
Laura was the first person Snowden reached out to anonymously in late 2012 when he decided to come forward with the information he later revealed and she was present during all the meetings between Snowden and Greenwald, as well as his lawyers.
The documentary makes for an almost surreal viewing experience with one of the most iconic scenes being Snowden sitting on his hotel bed in Hong Kong with his head entirely covered in a shirt while typing away on his laptop in order to protect himself from what he referred to as “visual surveillance”.
The documentary was nominated for 23 awards and won 16 of them, including an Oscar for “best documentary”.
One of the most appropriate reviews for this film in my opinion was given by Ronnie Scheib, the film critic of Variety magazine:
No amount of familiarity with whistleblower Edward Snowden and his shocking revelations of the U.S. government's wholesale spying on its own citizens can prepare one for the impact of Laura Poitras's extraordinary documentary Citizenfour...
far from reconstructing or analyzing a fait accompli, the film tersely records the deed in real time, as Poitras and fellow journalist Glenn Greenwald meet Snowden over an eight-day period in a Hong Kong hotel room to plot how and when they will unleash the bombshell that shook the world.
Adapting the cold language of data encryption to recount a dramatic saga of abuse of power and justified paranoia, Poitras brilliantly demonstrates that information is a weapon that cuts both ways.
You can watch this documentary in full below:
I watched it for the first time shortly after it came out and as I watched it again a few days ago, my altered view of reality over the last few years has really made it a profoundly disturbing experience.
Snowden warned us that there is a cancer quickly spreading across the so called “free world” and ten years later, that cancer is so far progressed that it can no longer be removed.
The only option we have left right now in my opinion is to start again from scratch:
A Great Reset is INEVITABLE!
Humanity has arrived to a fork in the road. It is my personal opinion that we have faced such forks many times before in our history (which is much much longer than what we have all been led to believe). This is another one. It could be the most important one yet but I’m just not sure to be honest as I believe we are a speci…












thanks for this discussion....I would add, sometimes even when you pay for the service, your info is still not safe. Currently on Protonmail free version. I have focused on getting the wifi out of my office, so paying for a 50 dolla fiber optic hard line from Quantum Fiber.....funny how they keep pushing me to 'upgrade' to wireless...though I have told them this multiple times.
Well, hell. I have been trying to get out of Apple Mail by going to Proton for some time now. Now I gotta transition out of Proton ... ugh. Where's that safe and effective Pony Express when you need it 😜
Thanks for an incredibly informative piece, Michael. Omg, where do you find the time?
~~ j ~~